New Android malware uses AI to click on hidden browser ads
- January 21, 2026
- 05:07 PM
- 0

A new family of Android click-fraud trojans leverages TensorFlow machine learning models to automatically detect and interact with specific advertisement elements.
The mechanism relies on visual analysis based on machine learning instead of predefined JavaScript click routines, and does not involve script-based DOM-level interaction like classic click-fraud trojans.
The threat actor is using TensorFlow.js, an open-source library developed by Google for training and deploying machine learning models in JavaScript. It permits running AI models in browsers or on servers using Node.js.
Researchers at mobile security company Dr.Web found that the new family of Android trojans is distributed through GetApps, the official app store for Xiaomi devices.
They discovered that the malware can operate in a mode called ‘phantom’, which uses a hidden WebView-based embedded browser to load a target page for click-fraud and a JavaScript file. The script’s purpose is to automate actions on the ads shown on the loaded site.
After loading the trained model from a remote server, the hidden browser is placed on a virtual screen, and screenshots are taken for TensorFlow.js to analyze and identify relevant elements.
By tapping on the correct UI element, the malware reproduces normal activity from a user. This method is more effective and resilient against modern ad variability, as most of these ads are dynamic, frequently change structure, and often use iframes or video.
A second mode, called ‘signalling’, uses WebRTC to stream a live video feed of the virtual browser screen to the attackers, allowing them to perform real-time actions like tapping, scrolling, and entering text.
The threat actor distributes the malware in games on Xiaomi’s GetApps software catalogue. Initially, the apps are submitted without malicious functionality and receive the malicious components in subsequent updates.
Some of the infected games identified by Doctor Web are:
- Theft Auto Mafia — 61,000 downloads
- Cute Pet House — 34,000 downloads
- Creation Magic World — 32,000 downloads
- Amazing Unicorn Party — 13,000 downloads
- Open World Gangsters — 11,000 downloads
- Sakura Dream Academy — 4,000 downloads
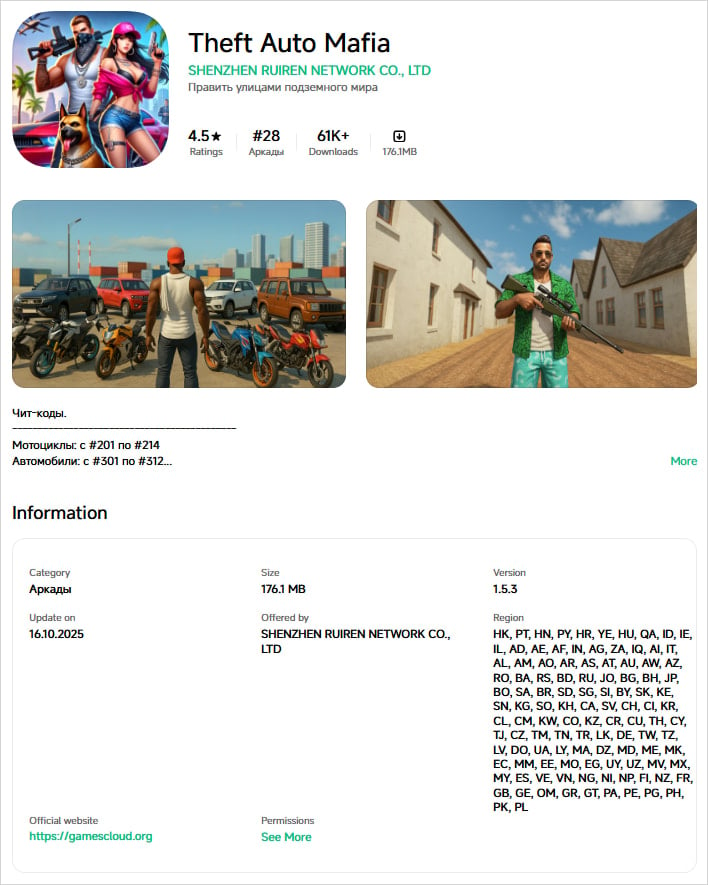
Source: Doctor Web
In addition to the Xiaomi-hosted apps, the trojans are distributed via third-party APK sites (e.g., Apkmody and Moddroid, altered versions, the so-called mods, of the original Spotify, YouTube, Deezer, and Netflix apps.
The researchers say that most apps on Moddroid’s “Editor’s Choice” page are infected.
Infected APK files are also distributed through Telegram channels, some app examples including Spotify Pro, Spotify Plus – Official, Moddroid.com, and Apkmody Chat.
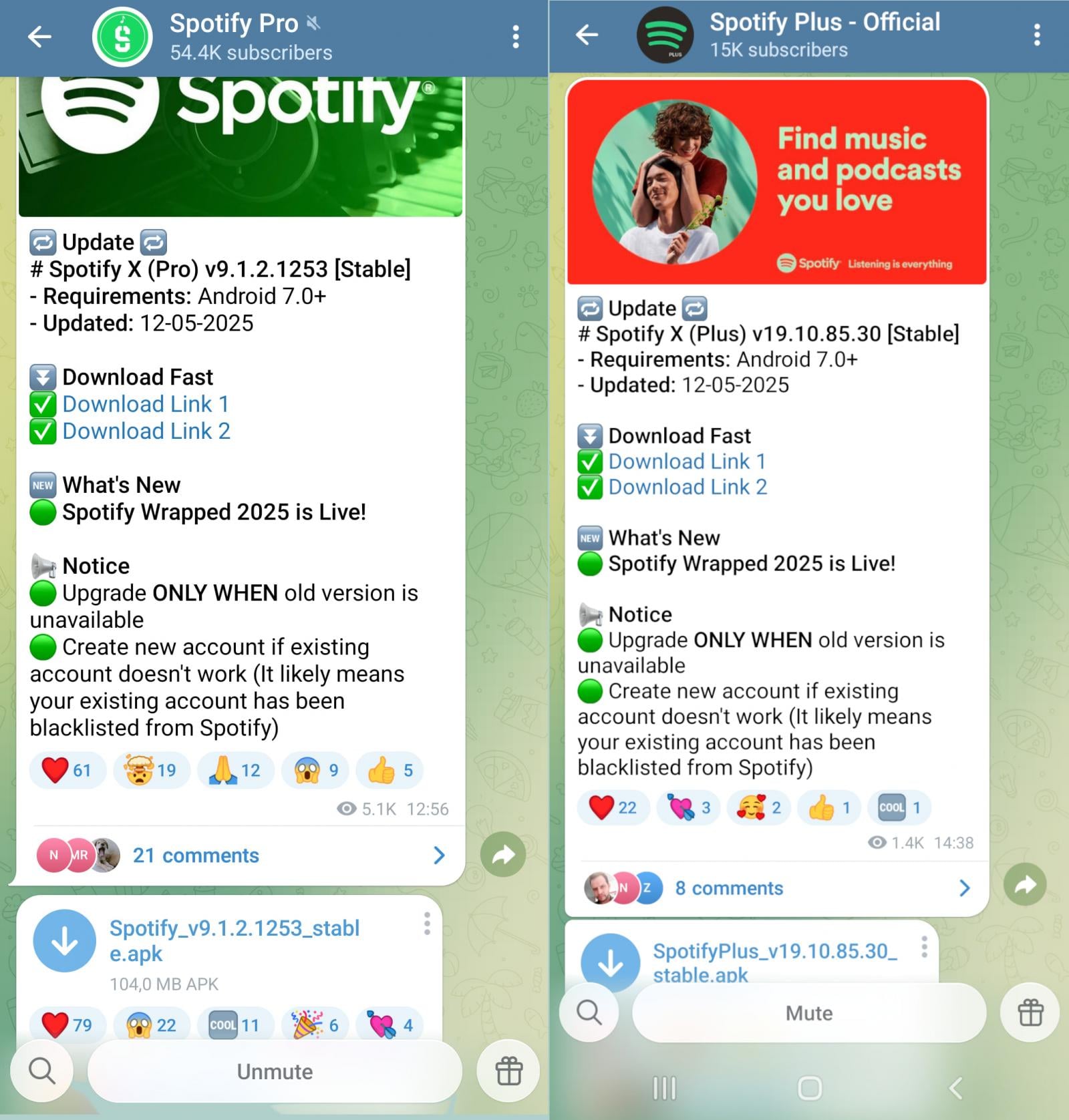
Source: Doctor Web
Dr.Web also found a Discord server with 24,000 subscribers pushing an infected app called Spotify X.
The researchers note that at least some of these apps “actually work,” which reduces users’ suspicion. Combined with the fact that click fraud is executed covertly in a hidden WebView rendering content on a virtual screen, this means that the victims will see no indication of the malicious activity.
Although clickjacking and ad fraud aren’t immediate threats to the user’s privacy and data, they are a lucrative cybercriminal activity. The direct impact on the user is battery drainage and premature degradation, and increased mobile data charges.
Android users are advised to avoid installing apps outside Google Play, especially alternative versions for popular apps that promise extra features or free access to premium subscriptions.
The 2026 CISO Budget Benchmark
It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
Source: www.bleepingcomputer.com

