Hackers exploit critical telnetd auth bypass flaw to get root
- January 23, 2026
- 11:21 AM
- 0
A coordinated campaign has been observed targeting a recently disclosed critical-severity vulnerability that has been present in the GNU InetUtils telnetd server for 11 years.
The security issue is tracked as CVE-2026-24061 and was reported on January 20. It is trivial to leverage and multiple exploit examples are publicly available.
Bug persisted since 2015
Open-source contributor Simon Josefsson explains that the telnetd component of GNU InetUtils contains a remote-authentication bypass vulnerability caused by unsanitized environment variable handling when spawning ‘/usr/bin/login.’
The flaw occurs because telnetd passes the user-controlled USER environment variable directly to login(1) without sanitization. By setting USER to -f root and connecting with the telnet -a command, an attacker can skip authentication and obtain root access.
The issue affects GNU InetUtils versions 1.9.3 (released in 2015) through 2.7, and was patched in version 2.8. For those who cannot upgrade to the safe release, mitigation strategies include disabling the telnetd service or blocking TCP port 23 on all firewalls.
GNU InetUtils is a collection of classic network client and server tools (telnet/telnetd, ftp/ftpd, rsh/rshd, ping, traceroute) maintained by the GNU Project, and used across multiple Linux distributions.
Although Telnet is an insecure, legacy component largely replaced by SSH, many Linux and Unix systems still include it for compatibility or specialized usage needs. It is particularly prevalent in the industrial sector because of its simplicity and low overhead.
On legacy and embedded devices, it can run without updates for more than a decade, explaining its presence in IoT devices, cameras, industrial sensors, and Operational Technology (OT) networks.
More technical users still rely on telnet for some projects:
Another user confirmed the use of telnet “to connect to older Cisco devices that are way past “End of Life.” Same SSH issue.”
However, devices exposed on the public internet that still have telnet active are scarce, prompting many researchers to describe the CVE-2026-24061 vulnerability as less critical.
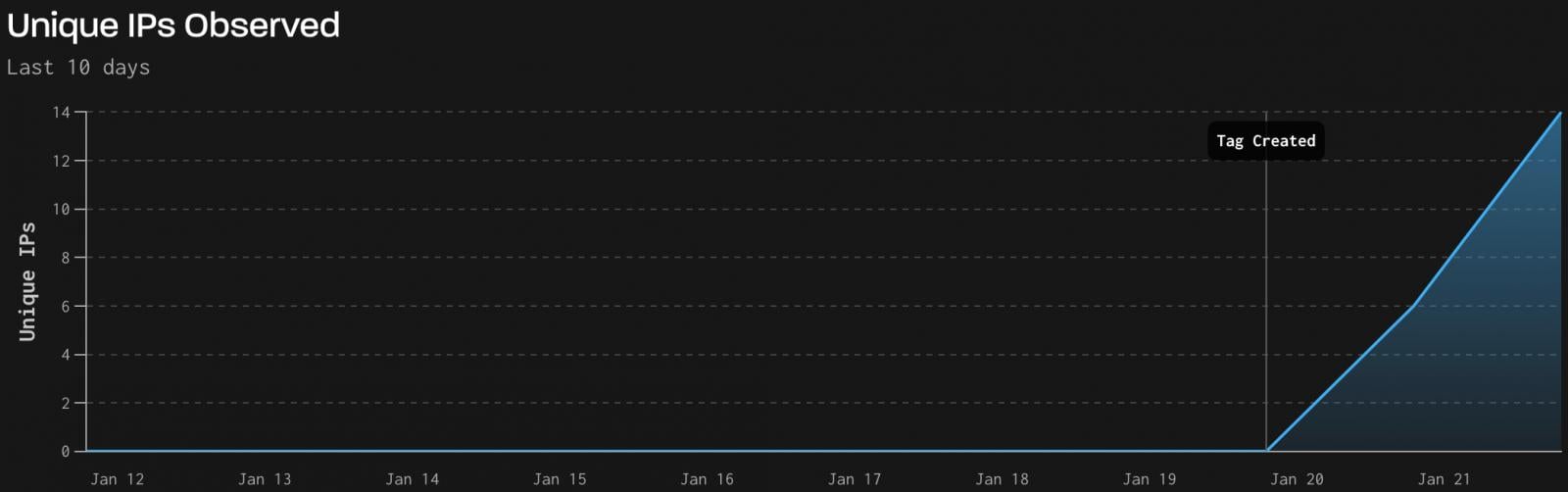
Threat monitoring firm GreyNoise reports that it has detected real-world exploitation activity leveraging CVE-2026-24061 against a small number of vulnerable endpoints.
The activity, logged between January 21 and 22, originated from 18 unique attacker IPs across 60 Telnet sessions, all deemed 100% malicious, sending 1,525 packets totaling 101.6 KB.
Source: GreyNoise
The attacks abuse the Telnet IAC option negotiation to inject ‘USER=-f <user>’ and grant shell access without authentication. GreyNoise says most of the activity appears automated, although it noted a few “human-at-keyboard” cases.
The attacks varied in terminal speed, type, and X11 DISPLAY values, but in 83.3% of the cases, they targeted the ‘root’ user.
In the post-exploitation phase, the attackers conducted automated reconnaissance and attempted to persist SSH keys and deploy Python malware. GreyNoise reports that these attempts failed on the observed systems due to missing binaries or directories.
While the exploitation activity appears limited in scope and success, potentially impacted systems should be patched or hardened as per the recommendations before the attackers optimize their attack chains.
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
Source: www.bleepingcomputer.com