VoidLink cloud malware shows clear signs of being AI-generated
- January 20, 2026
- 02:35 PM
- 0

The recently discovered cloud-focused VoidLink malware framework is believed to have been developed by a single person with the help of an artificial intelligence model.
Check Point Research published details about VoidLink last week, describing it as an advanced Linux malware framework that offers custom loaders, implants, rootkit modules for evasion, and dozens of plugins that expand its functionality.
The researchers highlighted the malware framework’s sophistication, assessing that it was likely the product of Chinese developers “with strong proficiency across multiple programming languages.”
In a follow-up report today, Check Point researchers say that there is “clear evidence that the malware was produced predominantly through AI-driven development” and reached a functional iteration within a week.
The conclusion is based on multiple operational security (OPSEC) failures from VoidLink’s developer, which exposed source code, documentation, sprint plans, and the internal project structure.
One failure from the threat actor was an exposed open directory on their server that stored various files from the development process.
“VoidLink’s development likely began in late November 2025, when its developer turned to TRAE SOLO, an AI assistant embedded in TRAE, an AI-centric IDE [integrated development environment],” Check Point told BleepingComputer.
Although the researchers did not have access to the complete conversation history in the IDE, they found on the threat actor’s server helper files from TRAE that included “key portions of the original guidance provided to the model.”
“Those TRAE-generated files appear to have been copied alongside the source code to the threat actor’s server, and later surfaced due to an exposed open directory. This leakage gave us unusually direct visibility into the project’s earliest directives,” Eli Smadja, Check Point Research Group Manager, told us.
According to the analysis, the threat actor used Spec-Driven Development (SDD) to define the project’s goals and set constraints, and had the AI generate a multi-team development plan covering architecture, sprints, and standards.
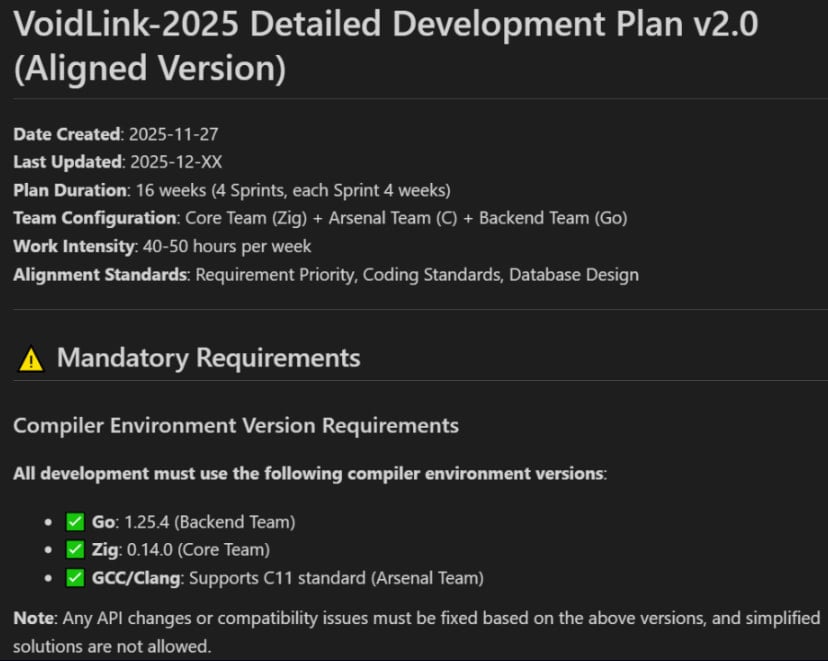
Source: Check Point
The malware developer then used that documentation as an execution blueprint for AI-generated code.
The generated documentation describes a 16-30 week, three-team effort, but based on timestamps and test artifacts timestamps that Check Point found, VoidLink was already functional within a week, reaching 88,000 lines of code by early December 2025.
.jpg)
Source: Check Point
Following this discovery, Check Point verified that the sprint specifications and the recovered source code match almost exactly, and researchers successfully reproduced the workflow, confirming that an AI agent can generate code that is structurally very similar to VoidLink’s.
Check Point says there’s “little room for doubt” about the origin of the codebase, describing VoidLink as the first documented example of an advanced malware that was generated by AI.
The researchers believe VoidLink marks a new era, where a single malware developer with strong technical knowledge can achieve results previously attainable only by well-resourced teams.
The 2026 CISO Budget Benchmark
It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
Source: www.bleepingcomputer.com

