Over 6,000 SmarterMail servers exposed to automated hijacking attacks
- January 27, 2026
- 09:09 AM
- 0

Nonprofit security organization Shadowserver has found over 6,000 SmarterMail servers exposed online and likely vulnerable to attacks exploiting a critical authentication bypass vulnerability.
Cybersecurity company watchTowr reported the security flaw to developer SmarterTools on January 8, which released a fix on January 15 without assigning an identifier.
The vulnerability was later assigned CVE-2026-23760 and rated critical severity, as it allows unauthenticated attackers to hijack admin accounts and gain remote code execution on the host, enabling them to take control of vulnerable servers.
“SmarterTools SmarterMail versions prior to build 9511 contain an authentication bypass vulnerability in the password reset API,” according to an advisory added to the NIST national vulnerability database on Thursday.
“The force-reset-password endpoint permits anonymous requests and fails to verify the existing password or a reset token when resetting system administrator accounts. An unauthenticated attacker can supply a target administrator username and a new password to reset the account, resulting in full administrative compromise of the SmarterMail instance.”
watchTowr discovered this auth bypass flaw two weeks after finding another critical pre-auth vulnerability in SmarterMail (CVE-2025-52691) that can allow attackers to gain remote code execution on unpatched servers.
On Monday, Shadowserver revealed that it’s tracking over 6,000 SmarterMail servers (more than 4,200 across North America and nearly 1,000 in Asia) flagged as “likely vulnerable” to ongoing CVE-2026-23760 attacks.
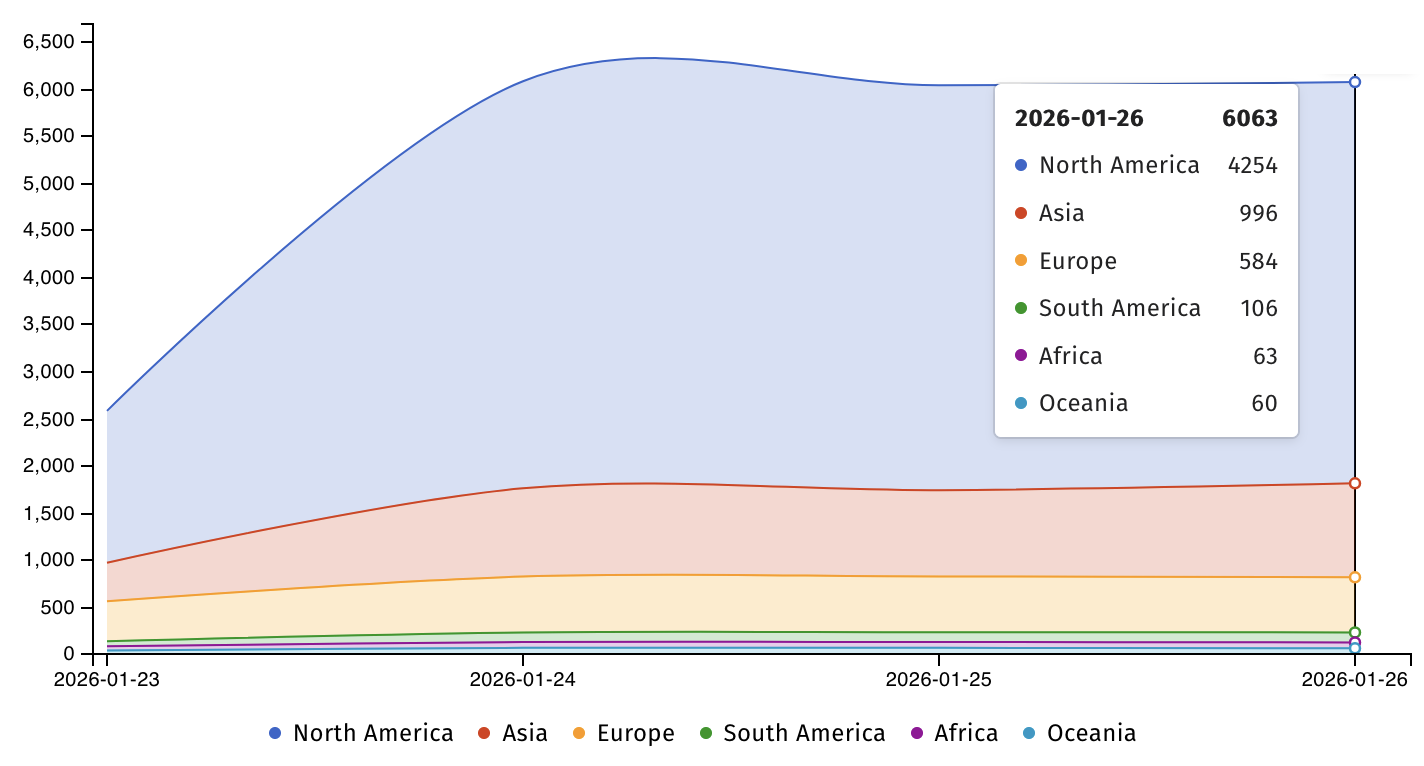
Macnica threat researcher Yutaka Sejiyama has also told BleepingComputer that his scans returned over 8,550 SmarterMail instances still vulnerable to CVE-2026-23760 attacks.
watchTowr, who shared a proof-of-concept exploit that only requires prior knowledge of the administrator account’s username, noted that it was tipped off about the flaw being exploited in the wild on January 21. Cybersecurity firm Huntress confirmed their report the next day, noting malicious attacks suggesting mass, automated exploitation.
On Monday, CISA added CVE-2026-23760 to its list of actively exploited vulnerabilities, ordering U.S. government agencies to secure their servers within three weeks, by February 16.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” CISA warned. “Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable.”
Yesterday, Shadowserver also reported finding almost 800,000 IP addresses with Telnet fingerprints amid ongoing attacks targeting a critical authentication bypass security flaw in the GNU Inetutils telnetd server.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
Source: www.bleepingcomputer.com

