WinRAR path traversal flaw still exploited by numerous hackers
- January 27, 2026
- 02:38 PM
- 2

Multiple threat actors, both state-sponsored and financially motivated, are exploiting the CVE-2025-8088 high-severity vulnerability in WinRAR for initial access and to deliver various malicious payloads.
The security issue is a path traversal flaw that leverages Alternate Data Streams (ADS) to write malicious files to arbitrary locations. Attackers have exploited this in the past to plant malware in the Windows Startup folder, for persistence across reboots.
Researchers at cybersecurity company ESET discovered the vulnerability and reported in early August 2025 that the Russia-aligned group RomCom had been exploiting it in zero-day attacks.
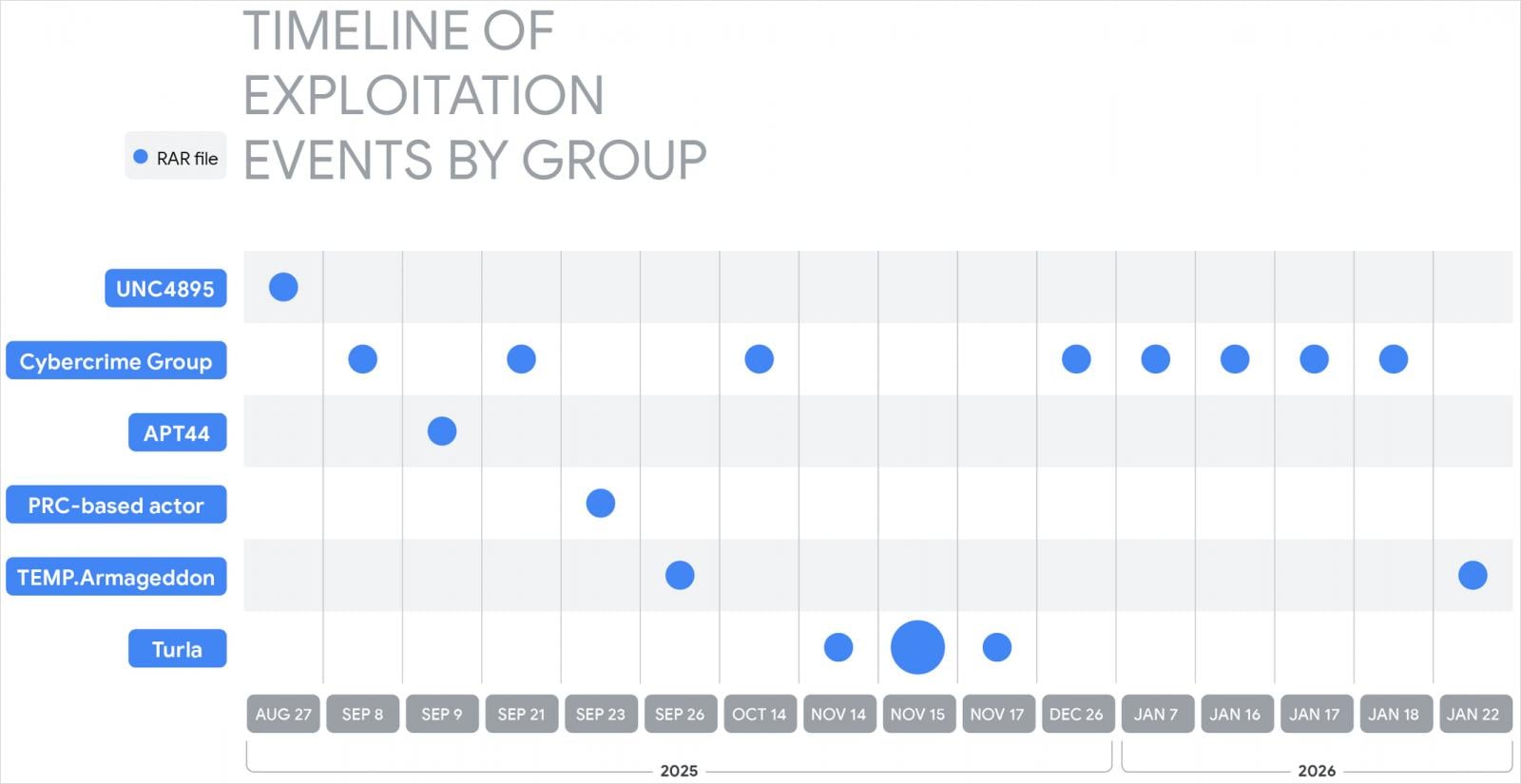
In a report today, the Google Threat Intelligence Group (GTIG) says that exploitation started as early as July 18, 2025, and continues to this day from both state-backed espionage actors and lower-tier, financially motivated cybercriminals.
“The exploit chain often involves concealing the malicious file within the ADS of a decoy file inside the archive.
“While the user typically views a decoy document, such as a PDF, within the archive, there are also malicious ADS entries, some containing a hidden payload while others are dummy data,” Google researchers explain.
When opened, WinRAR extracts the ADS payload using directory traversal, often dropping LNK, HTA, BAT, CMD, or script files that execute on user login.
Among the state-sponsored threat actors that Google researchers observed exploiting CVE-2025-8088 are:
- UNC4895 (RomCom/CIGAR) delivering NESTPACKER (Snipbot) via spearphishing to Ukrainian military units.
- APT44 (FROZENBARENTS) using malicious LNK files and Ukrainian-language decoys for follow-on downloads.
- TEMP.Armageddon (CARPATHIAN) dropping HTA downloaders into Startup folders (activity ongoing into 2026).
- Turla (SUMMIT) delivering the STOCKSTAY malware suite using Ukrainian army themes.
- China-linked actors using the exploit to deploy POISONIVY, dropped as a BAT file that downloads additional payloads.
Source: Google
Google also observed financially motivated actors exploiting the WinRAR path-traversal flaw to distribute commodity remote access tools and information stealers such as XWorm and AsyncRAT, Telegram bot-controlled backdoors, and malicious banking extensions for the Chrome browser.
All these threat actors are believed to have sourced working exploits from specialized suppliers, such as one using the alias “zeroplayer,” who advertised a WinRAR exploit last July.
The same threat actor has also marketed multiple high-value exploits last year, including alleged zero-days for Microsoft Office sandbox escape, corporate VPN RCE, Windows local privilege escalation, and bypasses for security solutions (EDR, antivirus), selling them for prices between $80,000 and $300,000.
Google comments that this reflects the commoditization of exploit development, which is crucial in the cyberattacks lifecycle, reducing the friction and complexity for attackers and enabling them to target unpatched systems in a short time.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
Source: www.bleepingcomputer.com

